Encrypted USBs have definitely come to the forefront in recent years when it comes to data protection and the way that organisations go about sharing information. There is still, however, a stigma about wanting to invest in such devices due to the fact that not much is really known about their capabilities. What do they actually do differently to a regular USB stick and what do all the different specifications around them mean? Phrases like '256-bit AES XTS encryption,' for instance, mean absolutely nothing to someone who has never bought an encrypted USB before: therefore, we've supplied some information to help individuals better understand the common specifications they will come across when they search for such devices.
AES encryption
AES stands for Advanced Encryption Standard and was first introduced back in 2001 by the US National Institute of Standards and Technology (NIST) as an algorithm designed to protect against various security attacks and hacking. The encryption is designed to “scramble” the contents of anything stored on the device, including personal data, in order to keep information secure from unauthorised personnel. It works like a padlock on the content, except to access it requires an individual to input a long string of characters.
There are 3 variations of AES encryption which offer different character lengths to access information: these are set at 128, 192, and 256 characters, with the latter being considered the best standard available.
So how does a cyber-criminal hack such a device? Well, technically it's close to impossible, as without any prior information they would need to go through up to 2^256 key variations in order to successfully hack into a device. Therefore, when you see 256-bit AES Encryption anywhere, you can be guaranteed it will offer the best possible standard of security available.
Hardware Encryption
There are various ways in which you can encrypt a USB device so it cannot be accessed by someone else. Cryptography software, such as Windows BitLocker and Veracrypt, can be used to add additional security to devices. However, software encrypted devices are only as strong as the computer they are used on. If the computer or operating system is at all compromised, the security provided by the encryption code will also be at risk. The encryption software can also be quite difficult to configure, especially for beginners who have no prior knowledge of how encryption works.
In contrast, Hardware Encrypted devices use their own separate, integrated security to perform encryption and decryption. As it operates separately to a computer it requires no additional software to function, which essentially means it cannot become vulnerable from malicious attacks or viruses. It is therefore highly recommended for portable devices such as USBs, or laptops that are used to carry around sensitive information. Hardware encrypted devices in general also require less configuration, which could be considered easier if companies are looking to use them throughout their organisation.
Partitions
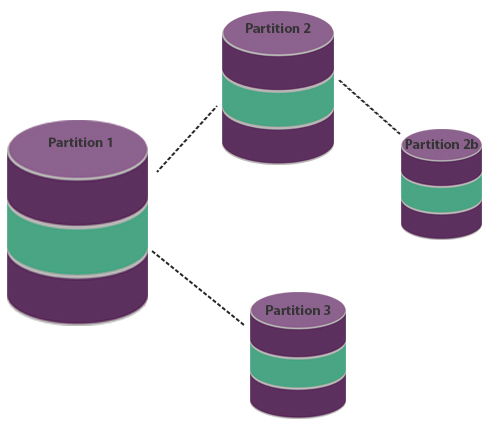
Put simply, partitions are pieces of information that have been grouped together into different areas on a drive so that they cannot be accessed all in one go. This is especially handy if you have more than one person using a single encrypted device and you do not want them to see all the information you have, and vice versa. It adds an additional layer of security, which means that even if a device is hacked not all the information may be compromised. For encrypted USBs, customers should look for devices which support multiple partitions wherever possible.
Anti Brute-Force Attack
A brute force attack is where a hacker or cybercriminal tries to discover a password by systematically trying every possible combination of letters, numbers, and/or symbols until they come across the correct combination. A password, in general, is never 100% secure, and given that many of us use something that is easily memorable to us, it becomes even more of an issue in modern society. Such attacks are easy to detect, but not as easy to prevent. This is where hardware encrypted devices come into their own, with many designed to automatically wipe the information on a flash drive after a failed number of password attempts has been reached. SafeToGo® Solo USBs, as one example, will delete the contents of a drive after 10 failed password attempts.
SafeConsole Compatibility
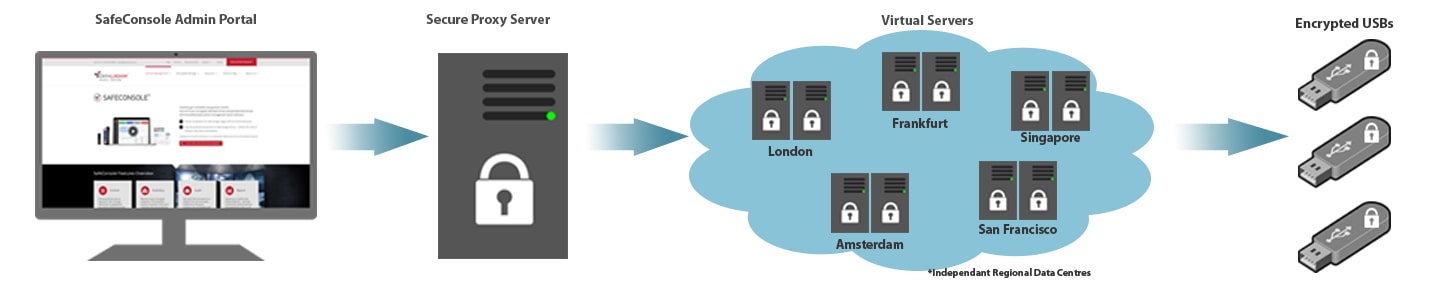
You may have seen this listed on some of our own encrypted devices. SafeConsole is a centralised management system designed to track all encrypted devices that an organisation may use. If, for example, you run a large national, or even international, organisation, SafeConsole will likely be beneficial in order to keep track of all data that is being shared or transferred among different users. The main benefit of this is that it offers complete control over encrypted devices, including how passwords are set-up, what content can be viewed and modified, and most importantly allow for such devices to be remotely wiped if they are ever lost or stolen, which in turn prevents data leaks from happening. The platform also enables you to ring-fence devices so that they can only be used within a certain area e.g up to 100 miles from the office base etc. Encrypted USBs such as the Kingston DataTraveler Privacy 3.0 or Kingston DataTraveler 4000 G2 are SafeConsole ready and therefore can be set up to work with this system.
FIPS Certification
FIPS stands for Federal Information Processing Standard. It is used in the US, Canada and the EU as a security standard against which software, hardware and firmware are measured, in regards to encryption. Currently, it is required by law that all US products used by the federal government for the purposes of cryptography (the official term) complete what's called a FIPS 140-2 validation before they can be used. Essentially it just adds that extra layer of approval to a product and gives customers that extra peace of mind.
Within the FIPS validation process, cryptography applications are tested against a number of criteria which ultimately determine what security level within the certification it will achieve, which run from level 1-4. Level one validated products meet the basic security requirements while level 4 offers the highest form of security, offering protection against all types of unauthorized physical access - essentially the device is capable of detecting environmental fluctuations outside of its normal operating parameters, in terms of voltage and temperature, and will wipe itself clean if it meets one of the these criteria.
Most USB flash drives will rate at level 2 or higher on the FIPS validation if they are hardware encrypted.
Generally speaking, it is not uncommon to find devices that are advertised as FIPs compliant rather than actually being certified due to the fact that it is not an essential requirement that devices have to adhere to. As well there is an inherently large cost associated with getting a product certified in the first place, therefore it should not be considered the only measure that an encrypted USB is any good.
Make sure to take a look at our comparison chart which shows how encrypted USB models such as the SafeToGo® Solo USB and Kingston DataTraveler Locker +G3 shapes up against other devices on the market based on some of the above specifications.